Here is a great video of Windows Azure Active Directory Premium.
Blog dedicated to Microsoft Infrastructure and more particularly to Active Directory, IdM and Security
mardi 24 décembre 2013
Top Solutions from Microsoft Support
Last month, an excellent Microsoft blog has appeared.
This blog is maintained by Microsoft Support for IT Pro and Developer products. These are the top content solutions we're providing to our customers to get important issues resolved. Solutions include KB articles, FixIT and hotfix articles, Technet and MSDN articles and blogs, Microsoft forums, and the Technet Wiki.
Here are direct links :
This blog is maintained by Microsoft Support for IT Pro and Developer products. These are the top content solutions we're providing to our customers to get important issues resolved. Solutions include KB articles, FixIT and hotfix articles, Technet and MSDN articles and blogs, Microsoft forums, and the Technet Wiki.
Here are direct links :
- Top Support Solutions for Microsoft Lync Server
- Top Support Solutions for Microsoft Forefront Unified Access Gateway (UAG)
- Top Support Solutions for Microsoft Windows 8
- Top Support Solutions for Microsoft Exchange Server
- Top Support Solutions for System Center Operations Manager
- Top Support Solutions for Microsoft Windows Server
- Top Support Solutions for System Center Configuration Manager
- Top Support Solutions for System Center Data Protection Manager (SCDPM)
- Top Support Solutions for System Center Virtual Machine Manager (SCVMM)
- Top Support Solutions for Microsoft SQL Server
- Top Support Solutions for Microsoft SharePoint Server
- Top Support Solutions for Microsoft System Center Endpoint Protection
- Top Support Solutions for Microsoft ForeFront Identity Manager
lundi 23 décembre 2013
[Rights Management Service] Microsoft Rights Management Service (RMS) whitepapers
Microsoft has updated its whitepapers on Rights Management Service.
Due to increased regulation, the Consumerization of IT (CoIT) and the “Bring Your Own Device” (BYOD), the explosion of information with dispersed enterprise data, the Social Enterprise and its applications enabling new collaboration, analytics scenarios, etc. enterprises of all sizes are facing growing needs to protect sensitive information. At the same time, enterprises have a need to securely share that same information amongst appropriate employees and other individuals within and outside the corporate network.
The NEW Microsoft Rights Management service (RMs) offering (microsoft.com/rms) provides the capability to create and consume protected content such as e-mail and documents of any type. Such a capability is available as a standalone subscription (for your on-premises infrastructure with the Microsoft Rights Management connector) or is part of the Office 365 Enterprise subscription, natively integrated with Exchange Online, SharePoint Online, and Microsoft Office to apply persistent protection to the content to meet the business requirements of your organization.
The Microsoft Rights Management suite is implemented as a Windows Azure service. Beyond the available RMS enlightened applications on the market, it comprises a set of Microsoft Rights Management sharing applications that work on all your common devices, a set of software development kits, and related tooling. By leveraging Windows Azure Active Directory, the cloud-hosted Microsoft Rights Management service acts as a trusted hub for secure collaboration where an organization can easily share information securely with other organizations without additional setup or configuration. The other organization(s) may be existing Microsoft Rights Management service’s customers but if not, they can use a free Microsoft Rights Management for individuals capability.
The whitepapers available as part of this download covers the various aspects of the offerings and provide in-depth information to evaluate or use the Microsoft Rights Management service and its components.
The whitepapers are available here : Microsoft Rights Management Service (RMS) whitepapers
Due to increased regulation, the Consumerization of IT (CoIT) and the “Bring Your Own Device” (BYOD), the explosion of information with dispersed enterprise data, the Social Enterprise and its applications enabling new collaboration, analytics scenarios, etc. enterprises of all sizes are facing growing needs to protect sensitive information. At the same time, enterprises have a need to securely share that same information amongst appropriate employees and other individuals within and outside the corporate network.
The NEW Microsoft Rights Management service (RMs) offering (microsoft.com/rms) provides the capability to create and consume protected content such as e-mail and documents of any type. Such a capability is available as a standalone subscription (for your on-premises infrastructure with the Microsoft Rights Management connector) or is part of the Office 365 Enterprise subscription, natively integrated with Exchange Online, SharePoint Online, and Microsoft Office to apply persistent protection to the content to meet the business requirements of your organization.
The Microsoft Rights Management suite is implemented as a Windows Azure service. Beyond the available RMS enlightened applications on the market, it comprises a set of Microsoft Rights Management sharing applications that work on all your common devices, a set of software development kits, and related tooling. By leveraging Windows Azure Active Directory, the cloud-hosted Microsoft Rights Management service acts as a trusted hub for secure collaboration where an organization can easily share information securely with other organizations without additional setup or configuration. The other organization(s) may be existing Microsoft Rights Management service’s customers but if not, they can use a free Microsoft Rights Management for individuals capability.
The whitepapers available as part of this download covers the various aspects of the offerings and provide in-depth information to evaluate or use the Microsoft Rights Management service and its components.
The whitepapers are available here : Microsoft Rights Management Service (RMS) whitepapers
[Windows Azure] Windows Azure Virtual Machine Readiness Assessment
Microsoft just released this assessment tool.
This assessment will automatically inspect your on-premises environment, whether it be bare metal or already virtualized. After that, we will provide you with tailored guidance and recommendations for migrating your environment to Windows Azure. If you’re running Active Directory, SQL, or SharePoint this tool will make it easy for you to get started.
The tool is available here : Windows Azure Virtual Machine Readiness Assessment
This assessment will automatically inspect your on-premises environment, whether it be bare metal or already virtualized. After that, we will provide you with tailored guidance and recommendations for migrating your environment to Windows Azure. If you’re running Active Directory, SQL, or SharePoint this tool will make it easy for you to get started.
The tool is available here : Windows Azure Virtual Machine Readiness Assessment
dimanche 22 décembre 2013
[Active Directory] Active Directory from on-premises to the cloud – Windows Azure AD whitepapers
Microsoft just released 4 whitepapers on Windows Azure AD.
Identity management, provisioning, role management, and authentication are key services both on-premises and through the (hybrid) cloud. With:
Windows Azure AD is the identity foundation for many Microsoft services like Office 365, Windows Intune, and others. Windows Azure AD is a comprehensive identity and access management cloud solution, utilizing the enterprise-grade quality and proven capabilities of Windows Server AD on-premises. It combines core directory services, advanced identity governance, security and application access management.
This series of whitepapers on Windows Azure AD offerings comprises:
An introduction on Windows Azure AD whitepaper further presents the capabilities that can be leveraged to centralize the identity management needs of your modern business applications, and your SaaS subscriptions, whether they are cloud-based, hybrid, or even on-premises. Windows Azure AD is a complete offering that can help you take advantage of your on-premises existing investment, fully outsource to the cloud your users (and devices) management and anything in between.
For enterprises with more demanding needs an advanced offering, Windows Azure Active Directory Premium, currently in preview, helps complete the set of capabilities that this identity and access management solution delivers.
Leverage Multi-Factor Authentication with Windows Azure AD whitepaper covers the Windows Azure Multi-Factor Authentication paid offering and how to leverage it with Windows Azure AD (Premium).
Leverage Windows Azure AD for modern Business Applications whitepaper further presents the aspects that relates to the development of solutions. Windows Azure AD offers to developers and cloud ISVs an identity management platform to deliver access control to their modern business applications, based on centralized policy and rules.
The whitepapers are available here : Active Directory from on-premises to the cloud – WAAD whitepapers
Identity management, provisioning, role management, and authentication are key services both on-premises and through the (hybrid) cloud. With:
- The Bring Your Own Apps (BYOA) for the cloud and the Software as a Service (SaaS) applications,
- The desire to better collaborate a la Facebook with the “social” enterprise,
- The need to support and integrate with social networks, which lead to a Bring Your Own Identity (BYOI) trend,
Windows Azure AD is the identity foundation for many Microsoft services like Office 365, Windows Intune, and others. Windows Azure AD is a comprehensive identity and access management cloud solution, utilizing the enterprise-grade quality and proven capabilities of Windows Server AD on-premises. It combines core directory services, advanced identity governance, security and application access management.
This series of whitepapers on Windows Azure AD offerings comprises:
- Active Directory from the on-premises to the cloud whitepaper.
- An overview of Windows Azure AD
- Leverage Multi-Factor Authentication with Windows Azure AD whitepaper.
- Leverage Windows Azure AD for modern Business Applications whitepaper.
An introduction on Windows Azure AD whitepaper further presents the capabilities that can be leveraged to centralize the identity management needs of your modern business applications, and your SaaS subscriptions, whether they are cloud-based, hybrid, or even on-premises. Windows Azure AD is a complete offering that can help you take advantage of your on-premises existing investment, fully outsource to the cloud your users (and devices) management and anything in between.
For enterprises with more demanding needs an advanced offering, Windows Azure Active Directory Premium, currently in preview, helps complete the set of capabilities that this identity and access management solution delivers.
Leverage Multi-Factor Authentication with Windows Azure AD whitepaper covers the Windows Azure Multi-Factor Authentication paid offering and how to leverage it with Windows Azure AD (Premium).
Leverage Windows Azure AD for modern Business Applications whitepaper further presents the aspects that relates to the development of solutions. Windows Azure AD offers to developers and cloud ISVs an identity management platform to deliver access control to their modern business applications, based on centralized policy and rules.
The whitepapers are available here : Active Directory from on-premises to the cloud – WAAD whitepapers
lundi 16 décembre 2013
[Security] PowerShell Security Best Practices
Lee Holmes just post an article on Windows Powershell Blog.
This article is about a presentation which was made at the BlueHat conference on Powershell Security Best Practices.
The presentation were recorded but won't be released publicly.
He give a link to the presentation deck, with very detailed speaker notes.
The blog post : PowerShell Security Best Practices
The Presentation : PowerShell Security Best Practices.pptx
This article is about a presentation which was made at the BlueHat conference on Powershell Security Best Practices.
The presentation were recorded but won't be released publicly.
He give a link to the presentation deck, with very detailed speaker notes.
The blog post : PowerShell Security Best Practices
The Presentation : PowerShell Security Best Practices.pptx
mercredi 13 novembre 2013
[Security] Microsoft Baseline Security Analyzer 2.3 available
Microsoft Baseline Security Analyzer 2.3 has been released.
MBSA 2.3 release adds support for Windows 8.1, Windows 8, Windows Server 2012 R2, and Windows Server 2012. Windows 2000 will no longer be supported with this release.
MBSA 2.3 runs on Windows 8.1, Windows Server 2012, and Windows Server 2012 R2, Windows Server 2008 R2, Windows 7, Windows Server 2008, Windows Vista, Windows Server 2003 and Windows XP systems and will scan for missing security updates, rollups and service packs using Microsoft Update technologies. To assess missing security updates, MBSA will only scan for missing security updates, update rollups and service packs available from Microsoft Update.
The tool is available here : Microsoft Baseline Security Analyzer 2.3
MBSA 2.3 release adds support for Windows 8.1, Windows 8, Windows Server 2012 R2, and Windows Server 2012. Windows 2000 will no longer be supported with this release.
MBSA 2.3 runs on Windows 8.1, Windows Server 2012, and Windows Server 2012 R2, Windows Server 2008 R2, Windows 7, Windows Server 2008, Windows Vista, Windows Server 2003 and Windows XP systems and will scan for missing security updates, rollups and service packs using Microsoft Update technologies. To assess missing security updates, MBSA will only scan for missing security updates, update rollups and service packs available from Microsoft Update.
The tool is available here : Microsoft Baseline Security Analyzer 2.3
[Security] Enhanced Mitigation Experience Toolkit 4.1 available
Enhanced Mitigation Experience Toolkit has been updated.
EMET 4.1 release includes new functionality and updates, such as:
EMET 4.1 is available here : Enhanced Mitigation Experience Toolkit 4.1
EMET 4.1 release includes new functionality and updates, such as:
- Updated default protection profiles, Certificate Trust rules, and Group Policy Object configuration.
- Shared remote desktop environments are now supported on Windows servers where EMET is installed.
- Windows Event logging mechanism allows for more accurate reporting in multi-user scenarios.
- Addressed several application-compatibility enhancements and mitigation false positive reporting.
EMET 4.1 is available here : Enhanced Mitigation Experience Toolkit 4.1
mardi 5 novembre 2013
[Active Directory] Windows Azure Active Directory Sync tool updated
Windows Azure Active Directory Sync tool has been updated.
Here are the changes :
As you can see, DirSync can now be installed on a Domain Controller.
Documentation can be found here : Directory Sync tool on a Domain Controller
The tool is available here : Windows Azure Active Directory Sync tool – 64 bit
Here are the changes :
- Fix to address Sync Engine memory leak
- Fix to address "staging-error" during full import from Azure Active Directory
- Fix to handle Read-Only Domain Controllers in Password Sync
- DirSync can be installed on a Domain Controller.
As you can see, DirSync can now be installed on a Domain Controller.
Documentation can be found here : Directory Sync tool on a Domain Controller
The tool is available here : Windows Azure Active Directory Sync tool – 64 bit
lundi 4 novembre 2013
[Security] Microsoft Security Intelligence Report Volume 15 (January - June 2013) available
Microsoft has released Volume 15 of the Microsoft Security Intelligence Report.
Microsoft Security Intelligence Report provides an in-depth perspective on malicious and potentially unwanted software, software exploits, security breaches and software vulnerabilities (both in Microsoft software and in third-party software). Microsoft developed these perspectives based on detailed analysis over the past several years, with a focus on the first half of 2013.
All reports are available here : Microsoft Security Intelligence Report Volume 15 (January - June 2013)
Microsoft Security Intelligence Report provides an in-depth perspective on malicious and potentially unwanted software, software exploits, security breaches and software vulnerabilities (both in Microsoft software and in third-party software). Microsoft developed these perspectives based on detailed analysis over the past several years, with a focus on the first half of 2013.
All reports are available here : Microsoft Security Intelligence Report Volume 15 (January - June 2013)
[Security] AppLocker Design Guide available
Last month, Microsoft released two whitepapers on AppLocker.
This guide describes the end-to-end process for developing, testing and deploying AppLocker in an organization of any size and regardless of their security requirements, in a way that minimizes the impact on the operation of the business.
The AppLocker Design Guide addresses how to establish trust between a computing platform and the code it is asked to run. While a number of techniques exist such as digital signing (to prove authenticity and integrity) and distribution through app stores (where apps can be vetted), these are not applied uniformly across the computing ecosystem and are not enforced by the end-user’s computer. Application whitelisting is increasingly recognized in the security community as a more effective alternative to the never-ending “arms race” between anti-malware vendors and the criminals who use malware as a tool in performing illegal activities.
AppLocker Design Guide consists of two whitepapers, 1.) AppLocker Design Guide, 2.) AppLocker Guide for Technical Decision Makers, as well as well as a sample AppLocker script plain text file.
The whitepapers are available here : AppLocker Design Guide
This guide describes the end-to-end process for developing, testing and deploying AppLocker in an organization of any size and regardless of their security requirements, in a way that minimizes the impact on the operation of the business.
The AppLocker Design Guide addresses how to establish trust between a computing platform and the code it is asked to run. While a number of techniques exist such as digital signing (to prove authenticity and integrity) and distribution through app stores (where apps can be vetted), these are not applied uniformly across the computing ecosystem and are not enforced by the end-user’s computer. Application whitelisting is increasingly recognized in the security community as a more effective alternative to the never-ending “arms race” between anti-malware vendors and the criminals who use malware as a tool in performing illegal activities.
AppLocker Design Guide consists of two whitepapers, 1.) AppLocker Design Guide, 2.) AppLocker Guide for Technical Decision Makers, as well as well as a sample AppLocker script plain text file.
The whitepapers are available here : AppLocker Design Guide
[Active Directory] Active Directory Replication Status Tool 1.1 available
Active Directory Replication Status Tool 1.1 is now available.
The Active Directory Replication Status Tool (ADREPLSTATUS) analyzes the replication status for domain controllers in an Active Directory domain or forest. ADREPLSTATUS displays data in a format that is similar to REPADMIN /SHOWREPL * /CSV imported into Excel but with significant enhancements.
Specific capabilities for this tool include:
- Expose Active Directory replication errors occurring in a domain or forest
- Prioritize errors that need to be resolved in order to avoid the creation of lingering objects in Active Directory forests
- Help administrators and support professionals resolve replication errors by linking to Active Directory replication troubleshooting content on Microsoft TechNet
- Allow replication data to be exported to source or destination domain administrators or support professionals for offline analysis
The tool is available here : Active Directory Replication Status Tool 1.1
mardi 18 juin 2013
[Security] Enhanced Mitigation Experience Toolkit 4.0 available
Enhanced Mitigation Experience Toolkit 4.0 is available.
The Enhanced Mitigation Experience Toolkit (EMET) is designed to help prevent hackers from gaining access to your system.
Software vulnerabilities and exploits have become an everyday part of life. Virtually every product has to deal with them and consequently, users are faced with a stream of security updates. For users who get attacked before the latest updates have been applied or who get attacked before an update is even available, the results can be devastating: malware, loss of PII, etc.
Security mitigation technologies are designed to make it more difficult for an attacker to exploit vulnerabilities in a given piece of software. EMET allows users to manage these technologies on their system and provides several unique benefits:
The toolkit includes several pseudo mitigation technologies aimed at disrupting current exploit techniques. These pseudo mitigations are not robust enough to stop future exploit techniques, but can help prevent users from being compromised by many of the exploits currently in use. The mitigations are also designed so that they can be easily updated as attackers start using new exploit techniques.
Below is a summary of the features and changes that are included with the EMET 4.0 release:
EMET 4.0 also includes bug fixes and UI changes to improve the overall user experience. Also, at the end of the installation, EMET will offer the user to automatically apply recommended settings to protect Internet Explorer, Microsoft Office, Adobe Acrobat/Reader, and Oracle Java, as well as a pre-defined set of rules for the Certificate Trust feature that will monitor the main Microsoft and other popular online services. More information are available in the User Guide, available in the EMET installation folder.
The tool is available here : Enhanced Mitigation Experience Toolkit 4.0
The Enhanced Mitigation Experience Toolkit (EMET) is designed to help prevent hackers from gaining access to your system.
Software vulnerabilities and exploits have become an everyday part of life. Virtually every product has to deal with them and consequently, users are faced with a stream of security updates. For users who get attacked before the latest updates have been applied or who get attacked before an update is even available, the results can be devastating: malware, loss of PII, etc.
Security mitigation technologies are designed to make it more difficult for an attacker to exploit vulnerabilities in a given piece of software. EMET allows users to manage these technologies on their system and provides several unique benefits:
- No source code needed: Until now, several of the available mitigations (such as Data Execution Prevention) have required for an application to be manually opted in and recompiled. EMET changes this by allowing a user to opt in applications without recompilation. This is especially handy for deploying mitigations on software that was written before the mitigations were available and when source code is not available.
- Highly configurable: EMET provides a higher degree of granularity by allowing mitigations to be individually applied on a per process basis. There is no need to enable an entire product or suite of applications. This is helpful in situations where a process is not compatible with a particular mitigation technology. When that happens, a user can simply turn that mitigation off for that process.
- Helps harden legacy applications: It’s not uncommon to have a hard dependency on old legacy software that cannot easily be rewritten and needs to be phased out slowly. Unfortunately, this can easily pose a security risk as legacy software is notorious for having security vulnerabilities. While the real solution to this is migrating away from the legacy software, EMET can help manage the risk while this is occurring by making it harder to hackers to exploit vulnerabilities in the legacy software.
- Ease of use: The policy for system wide mitigations can be seen and configured with EMET's graphical user interface. There is no need to locate up and decipher registry keys or run platform dependent utilities. With EMET you can adjust setting with a single consistent interface regardless of the underlying platform.
- Ease of deploy: EMET comes with built-in support for enterprise deployment and configuration technologies. This enables administrators to use Group Policy or System Center Configuration Manager to deploy, configure and monitor EMET installations across the enterprise environment.
- Ongoing improvement: EMET is a living tool designed to be updated as new mitigation technologies become available. This provides a chance for users to try out and benefit from cutting edge mitigations. The release cycle for EMET is also not tied to any product. EMET updates can be made dynamically as soon as new mitigations are ready
The toolkit includes several pseudo mitigation technologies aimed at disrupting current exploit techniques. These pseudo mitigations are not robust enough to stop future exploit techniques, but can help prevent users from being compromised by many of the exploits currently in use. The mitigations are also designed so that they can be easily updated as attackers start using new exploit techniques.
Below is a summary of the features and changes that are included with the EMET 4.0 release:
- Certificate Trust: considering the raise of PKI-related attacks, we decided to implement a configurable SSL Certificate Pinning to try to detect Man in the Middle attacks that leverage SSL/TLS certificates. The Certificate Trust feature in EMET is rule-based and allows to pin a specific SSL/TLS certificate to a trusted Root Certificate Authority.
- ROP mitigations and hardening: in the last Technical Preview release of EMET, we introduced some mitigations to try to stop ROP-based attacks by implementing some of the winner ideas of the BlueHat Prize contest. With this new EMET release we hardened the ROP and other mitigations to detect and stop novel attack techniques.
- Early Warning Program: this feature will allow EMET to send contextual data back to Microsoft, through the standard Windows Error Reporting channel, every time that an exploit has been detected and stopped. We are adding this feature to help us respond to new 0day exploits as soon as possible.
- Audit mode: if an exploit is detected, EMET will not terminate the attacked process but it will just report the attack and let the process continue. This mode is only applicable to certain mitigations, for example the anti-ROP ones, that detect the attack when the process is not already in a crashed state. This feature is useful for enterprise customers for testing purposes and to spot false-positives and app-compat problems without compromising the user experience.
EMET 4.0 also includes bug fixes and UI changes to improve the overall user experience. Also, at the end of the installation, EMET will offer the user to automatically apply recommended settings to protect Internet Explorer, Microsoft Office, Adobe Acrobat/Reader, and Oracle Java, as well as a pre-defined set of rules for the Certificate Trust feature that will monitor the main Microsoft and other popular online services. More information are available in the User Guide, available in the EMET installation folder.
The tool is available here : Enhanced Mitigation Experience Toolkit 4.0
jeudi 13 juin 2013
[Security] Mitigating Pass-the-Hash (PtH) Attacks and Other Credential Theft Techniques updated
The white paper "Mitigating Pass-the-Hash (PtH) Attacks and Other Credential Theft Techniques" has been updated.
The new version of this document is available here : Mitigating Pass-the-Hash (PtH) Attacks and Other Credential Theft Techniques
The new version of this document is available here : Mitigating Pass-the-Hash (PtH) Attacks and Other Credential Theft Techniques
mardi 4 juin 2013
[Windows Server] Windows Server 2012 R2 announced and WS 2012 R2 Overview White Paper released
Microsoft has just presented Windows Server 2012 R2 and released its overview White Paper.
At the heart of the Microsoft Cloud OS vision, Windows Server 2012 R2 brings Microsoft’s experience delivering global-scale cloud services into your infrastructure. Windows Server 2012 R2 offers exciting new features and enhancements across virtualization, storage, networking, virtual desktop infrastructure, access and information protection, and more. Windows Server 2012 R2 is currently in preview and will be available soon for evaluation purposes.
Enterprise-class
New and enhanced features allow you to take advantage of even better performance and more efficient capacity utilization in your datacenter, helping you increase the agility of your business. Windows Server 2012 R2 offers a proven, enterprise-class virtualization and cloud platform that can scale to continuously run your largest workloads while enabling robust recovery options to protect against service outages.
Simple and cost-effective
Windows Server 2012 R2 also gives you resilient, multi-tenant-aware storage and networking capabilities for a wide range of workloads. It delivers these capabilities at a fraction of the cost of other solutions, through the use of low-cost, industry-standard hardware. With automation of a broad set of management tasks built-in, Windows Server 2012 R2 simplifies the deployment of major workloads and increases operational efficiencies.
Application focused
Windows Server 2012 R2 helps you build, deploy and scale applications and web sites quickly, and with more flexibility than ever before. In concert with Windows Azure VM and System Center 2012 R2, it unlocks improved application portability between on-premises environments and public and service provider clouds, increasing flexibility and elasticity of your IT services. Windows Server 2012 R2 provides a scalable, highly available platform for mission-critical applications and offers enhanced support for open standards, open source applications and various development languages.
User-centric
Windows Server 2012 R2 makes it easier to deploy a virtual desktop infrastructure, and can lower storage costs significantly by supporting a broad range of storage options and VHD de-duplication. Virtual Desktop Infrastructure in Windows Server 2012 R2 makes it possible for users to access IT from virtually anywhere, providing them a rich Windows experience while ensuring enhanced data security and compliance.
Windows Server 2012 R2 enables you to provide access to corporate resources and helps protect critical business information. With Windows Server 2012 R2, you can manage identities across your datacenter and federated into the cloud, provide flexible remote access to applications and resources, and define the resources and level of access users have to information based on who they are, what they are accessing, and what device they are using.
Here is the Windows Server 2012 R2 white paper : Windows Server 2012 R2 Overview White Paper
Overview
At the heart of the Microsoft Cloud OS vision, Windows Server 2012 R2 brings Microsoft’s experience delivering global-scale cloud services into your infrastructure. Windows Server 2012 R2 offers exciting new features and enhancements across virtualization, storage, networking, virtual desktop infrastructure, access and information protection, and more. Windows Server 2012 R2 is currently in preview and will be available soon for evaluation purposes.
Benefits
Enterprise-class
New and enhanced features allow you to take advantage of even better performance and more efficient capacity utilization in your datacenter, helping you increase the agility of your business. Windows Server 2012 R2 offers a proven, enterprise-class virtualization and cloud platform that can scale to continuously run your largest workloads while enabling robust recovery options to protect against service outages.
Simple and cost-effective
Windows Server 2012 R2 also gives you resilient, multi-tenant-aware storage and networking capabilities for a wide range of workloads. It delivers these capabilities at a fraction of the cost of other solutions, through the use of low-cost, industry-standard hardware. With automation of a broad set of management tasks built-in, Windows Server 2012 R2 simplifies the deployment of major workloads and increases operational efficiencies.
Application focused
Windows Server 2012 R2 helps you build, deploy and scale applications and web sites quickly, and with more flexibility than ever before. In concert with Windows Azure VM and System Center 2012 R2, it unlocks improved application portability between on-premises environments and public and service provider clouds, increasing flexibility and elasticity of your IT services. Windows Server 2012 R2 provides a scalable, highly available platform for mission-critical applications and offers enhanced support for open standards, open source applications and various development languages.
User-centric
Windows Server 2012 R2 makes it easier to deploy a virtual desktop infrastructure, and can lower storage costs significantly by supporting a broad range of storage options and VHD de-duplication. Virtual Desktop Infrastructure in Windows Server 2012 R2 makes it possible for users to access IT from virtually anywhere, providing them a rich Windows experience while ensuring enhanced data security and compliance.
Windows Server 2012 R2 enables you to provide access to corporate resources and helps protect critical business information. With Windows Server 2012 R2, you can manage identities across your datacenter and federated into the cloud, provide flexible remote access to applications and resources, and define the resources and level of access users have to information based on who they are, what they are accessing, and what device they are using.
Here is the Windows Server 2012 R2 white paper : Windows Server 2012 R2 Overview White Paper
lundi 27 mai 2013
[Microsoft Solution Accelerators] Microsoft Assessment and Planning Toolkit 8.5 Beta available
Microsoft Assessment and Planning Toolkit 8.5 Beta is available.
Accelerate your Windows Server 2012 migration with MAP 8.5 Beta!
Accelerate your Windows Server 2012 migration with Microsoft Assessment and Planning (MAP) Toolkit 8.5. This latest version of MAP adds new scenarios to help plan your environment with agility and focus while lowering the cost of delivering IT. Included in MAP 8.5 are hardware and infrastructure readiness assessments to assist you in planning the deployment of Windows 8 and Windows Server 2012, preparing your migration to Windows Azure Virtual Machines, readying your environment for Office 2013 and Office 365, and tracking your usage of Windows Server, Lync, SharePoint, and Exchange.
Key features and benefits of MAP 8.5 Beta help you:
Key features and benefits in more detail:
Newly designed user interface
The MAP Toolkit 8.5 Beta features a newly designed user interface which provides a more intuitive user experience. Scenarios have been organized into Scenario Groups to allow quick navigation and display at-a-glance summaries on individual scenario tiles. Details for each scenario can be found in the Scenario Detail Pages along with a checklist of steps needed to maximize your results and enable one-click report generation.
Lync 2013, SharePoint 2013, and Exchange 2013 Usage Tracking Support
Groundbreaking new releases of Lync, SharePoint, and Exchange have been brought to market this year. These products enable IT organizations and their end users greater efficiency, productivity and flexibility than ever before. With the release of the MAP Toolkit 8.5 Beta, the usage tracking scenarios within MAP have been updated to leverage new usage tracking capabilities provided within Lync, SharePoint, and Exchange resulting in less administrative effort and greater accuracy to collect and report on end user access to these servers.
Enhanced Virtual Machine discovery
Server virtualization has become the standard method for optimizing an organization's resource utilization, availability, and agility. The MAP Toolkit 8.5 Beta assists in the effort to virtualize with added discoverability of virtual machines for software asset location and reporting to facilitate license compliance for highly virtualized environments. Additionally, the MAP Toolkit now includes enhanced inventory reports which detail the virtual machines discovered, as well as the total number of virtual machines running on each host.
Windows Volume Licensing scenario helps to Identify license status of computers running Windows Vista SP1 and newer
Microsoft Volume Licensing gives you flexible, cost-effective access to the Microsoft products and services that your business is built upon. The MAP Toolkit 8.5 Beta provides the ability to detect and report on the volume license status of client computers in your enterprise so you can rest assured that you are in full compliance with your volume license agreement.
The tool is available here : Microsoft Assessment and Planning Toolkit 8.5 Beta
Accelerate your Windows Server 2012 migration with MAP 8.5 Beta!
Accelerate your Windows Server 2012 migration with Microsoft Assessment and Planning (MAP) Toolkit 8.5. This latest version of MAP adds new scenarios to help plan your environment with agility and focus while lowering the cost of delivering IT. Included in MAP 8.5 are hardware and infrastructure readiness assessments to assist you in planning the deployment of Windows 8 and Windows Server 2012, preparing your migration to Windows Azure Virtual Machines, readying your environment for Office 2013 and Office 365, and tracking your usage of Windows Server, Lync, SharePoint, and Exchange.
Key features and benefits of MAP 8.5 Beta help you:
- Newly designed user interface makes it easier to find and use the right MAP scenario for the task at hand.
- Usage tracking scenarios for Lync, SharePoint and Exchange have been updated to include the latest versions.
- Advances in virtual machine discovery offer improved VM inventory results.
- New Windows Volume Licensing scenario helps identify the licensing status of your desktop computers.
Key features and benefits in more detail:
Newly designed user interface
The MAP Toolkit 8.5 Beta features a newly designed user interface which provides a more intuitive user experience. Scenarios have been organized into Scenario Groups to allow quick navigation and display at-a-glance summaries on individual scenario tiles. Details for each scenario can be found in the Scenario Detail Pages along with a checklist of steps needed to maximize your results and enable one-click report generation.
Lync 2013, SharePoint 2013, and Exchange 2013 Usage Tracking Support
Groundbreaking new releases of Lync, SharePoint, and Exchange have been brought to market this year. These products enable IT organizations and their end users greater efficiency, productivity and flexibility than ever before. With the release of the MAP Toolkit 8.5 Beta, the usage tracking scenarios within MAP have been updated to leverage new usage tracking capabilities provided within Lync, SharePoint, and Exchange resulting in less administrative effort and greater accuracy to collect and report on end user access to these servers.
Enhanced Virtual Machine discovery
Server virtualization has become the standard method for optimizing an organization's resource utilization, availability, and agility. The MAP Toolkit 8.5 Beta assists in the effort to virtualize with added discoverability of virtual machines for software asset location and reporting to facilitate license compliance for highly virtualized environments. Additionally, the MAP Toolkit now includes enhanced inventory reports which detail the virtual machines discovered, as well as the total number of virtual machines running on each host.
Windows Volume Licensing scenario helps to Identify license status of computers running Windows Vista SP1 and newer
Microsoft Volume Licensing gives you flexible, cost-effective access to the Microsoft products and services that your business is built upon. The MAP Toolkit 8.5 Beta provides the ability to detect and report on the volume license status of client computers in your enterprise so you can rest assured that you are in full compliance with your volume license agreement.
The tool is available here : Microsoft Assessment and Planning Toolkit 8.5 Beta
[Active Directory] Hiding Data in Active Directory
Here is an interesting blog series from Guido Grillenmeier presenting differents way to hide data in Active Directory.
Here are the 4 parts :
Here are the 4 parts :
- Hiding Data in Active Directory
- Hiding Active Directory Objects and Attributes
- Enabling List Object Mode in a Forest
- Using the Confidentiality Bit to Hide Data in Active Directory
mardi 14 mai 2013
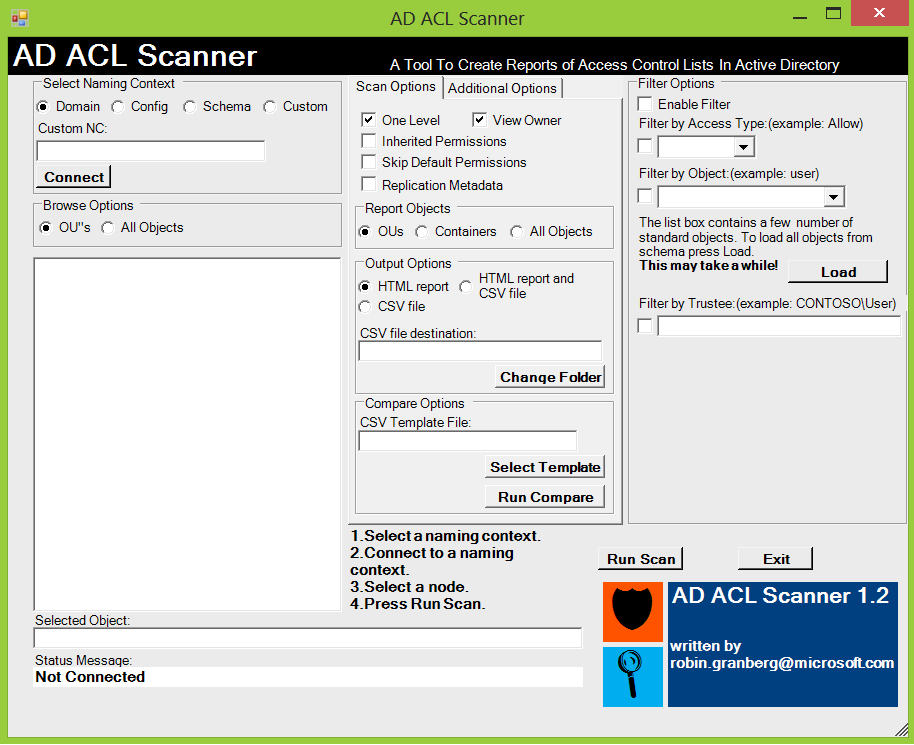
[Active Directory] AD ACL Scanner Tool
Robin Grandberg from Platform PFE's in Sweden Blog has released a great tool to create reports of access control lists in Active Directory.
This tool has the following features:
For more information : Take Control Over AD Permissions and the AD ACL Scanner Tool
The tool is available here : https://adaclscan.codeplex.com/
This tool has the following features:
- View HTML reports of ACLs and save it to disk.
- Export ACLs on Active Directory objects in a CSV format.
- Connect and browse you default domain, schema , configuration or a naming context defined by distinguishedname.
- Browse naming context by clicking you way around, either by OU’s or all types of objects.
- Report only explicitly assigned ACLs.
- Report on OUs , OUs and Container Objects or all object types.
- Filter ACLs for a specific access type.. Where does “Deny” permission exists?
- Filter ACLs for a specific identity. Where does "Domain\Client Admins" have explicit access?
- Filter ACLs for permission on specific object. Where are permissions set on computer objects?
- Skip default permissions (defaultSecurityDescriptor) in report. Makes it easier to find custom permissions.
- Report owner of object.
- Compare previous results with the current configuration and see the differences by color scheme (Green=matching permissions, Yellow= new permissions, Red= missing permissions).
- Report when permissions were modified
- Can use AD replication metadata when comparing.
- Can convert a previously created CSV file to a HTML report.
For more information : Take Control Over AD Permissions and the AD ACL Scanner Tool
The tool is available here : https://adaclscan.codeplex.com/
lundi 13 mai 2013
[Active Directory] Deploying Office 365 Single Sign-On using Windows Azure
Microsoft has just published this new document.
This document is intended for system architects and IT professionals who want to understand the architecture and deployment options for extending the on-premises Active Directory infrastructure with Windows Azure Virtual Machines to implement directory synchronization and single sign-on for Office 365.
The document is available here : Deploying Office 365 Single Sign-On using Windows Azure
This document is intended for system architects and IT professionals who want to understand the architecture and deployment options for extending the on-premises Active Directory infrastructure with Windows Azure Virtual Machines to implement directory synchronization and single sign-on for Office 365.
The document is available here : Deploying Office 365 Single Sign-On using Windows Azure
samedi 11 mai 2013
[Security] System Hardening Part 1
I would like to start a new blog series about this subject that I find very important and which isn't well documented. This blog series will only deal with Microsoft's systems but system hardening apply to all systems.
What is System Hardening ?
System Hardening (or OS Hardening) is the process to address the weaknesses and security vulnerabilities in operating systems.
System Hardening is performed by applying the latest patches and updates as well as follow specific
procedures and policies to reduce the attack surface of the system.
Why should you use System Hardening and what are benefits ?
If you ask an IT guy about security level in its company, he’ll mostly say that there are Firewalls, IDS/IPS, Anti-Virus, Updates policies, Proxy/Reverse Proxy, VPN, DMZ and that they feel safe with that.
Most of companies I worked for don’t know about system hardening. And when they have heard of it, they think it’s too complex to implement or they feel safe enough to not use it.
But you have to consider the following assumptions :
- What will happen if someone gets in your infrastructure ?
- What will happen if one of your employees turns rogue ?
- Are you sure all your systems are configured the same way and well-configured ?
ALL systems have weakness and vulnerabilities, system hardening will help mitigate external and internal threats but also misconfigurations.
System Hardening will help you to :
- Increase the level of infrastructure security
- Enhance the availability of infrastructure
- Be compliant with best practice
- Improve infrastructure performance
- Avoid misconfigurations
So if you are concerned by security, you have to implement System Hardening.
What next ?
Later in this blog series I will present you some tools which can help you to implement System Hardening.
For today, I'll finish this post by presenting a tool which can help you to measure security level of your infrastructure : Microsoft Security Assessment Tool 4.0
Even if this tool isn't System Hardening related, it's an interesting tool.
The Microsoft Security Assessment Tool (MSAT) is a risk-assessment application designed to provide information and recommendations about best practices for security within an information technology (IT) infrastructure.
The tool employs a holistic approach to measuring your security posture by covering topics across people, process, and technology. Findings are coupled with prescriptive guidance and recommended mitigation efforts, including links to more information for additional industry guidance. These resources may assist you in keeping you aware of specific tools and methods that can help change the security posture of your IT environment.
This tool is available here : Microsoft Security Assessment Tool 4.0
First you have defined your company's profile (approximately 50 questions).
After that, you could make the security assessment.
It could be interesting to do several assessment with different persons like CTO, CISO, IT Architect ... to see their personnal vision of the company's security level.
After you finished the assesment you get a summary report of your security level.
A full detailed report is also available and which could be exported.
And you can also upload anonymously your assessment and compare results with other companies.
That's it for this first part,we'll see in the next part which tools you can use to implement System Hardening.
vendredi 10 mai 2013
[Security] 2 new security documents published by the NSA
The National Security Agency has published in march 2 new documents about security.
The first one is titled "Spotting the Adversary with Windows Event Log Monitoring".
This white paper provides an introduction to collecting important Windows workstation event logs and storing them in a central location for easier searching and monitoring of network health using the built-in tools already available in the Microsoft Windows operating system.
The first document is available here : Spotting the Adversary with Windows Event Log Monitoring
The second one is titled "Reducing the Effectiveness of Pass-the-Hash"
In December 2012, Microsoft released a whitepaper which discusses PtH in-depth (available here : Mitigating Pass-the-Hash (PtH) Attacks and Other Credential Theft Techniques ), identifies numerous risk factors that make an organization highly vulnerable to PtH, and describes several mitigations. The purpose of this document is to expand on the ideas presented in the Microsoft's white paper and to provide guidance.
The second document is available here : Reducing the Effectiveness of Pass-the-Hash
The first one is titled "Spotting the Adversary with Windows Event Log Monitoring".
This white paper provides an introduction to collecting important Windows workstation event logs and storing them in a central location for easier searching and monitoring of network health using the built-in tools already available in the Microsoft Windows operating system.
The first document is available here : Spotting the Adversary with Windows Event Log Monitoring
The second one is titled "Reducing the Effectiveness of Pass-the-Hash"
In December 2012, Microsoft released a whitepaper which discusses PtH in-depth (available here : Mitigating Pass-the-Hash (PtH) Attacks and Other Credential Theft Techniques ), identifies numerous risk factors that make an organization highly vulnerable to PtH, and describes several mitigations. The purpose of this document is to expand on the ideas presented in the Microsoft's white paper and to provide guidance.
The second document is available here : Reducing the Effectiveness of Pass-the-Hash
jeudi 9 mai 2013
[Active Directory] Windows Azure Active Directory Videos
I've already blog about WAAD cartoon in january ( see : Windows Azure Active Directory Cartoon )
4 new videos are available at Channel 9 :
4 new videos are available at Channel 9 :
mercredi 1 mai 2013
[Active Directory] Windows Server 2012: Planning for Active Directory Forest Recovery White Paper Updated
Microsoft has updated Planning for Active Directory Forest Recovery White Paper for Windows Server 2012.
This guide contains best-practice recommendations for recovering an Active Directory forest, if forest-wide failure has rendered all domain controllers in the forest incapable of functioning normally. The procedure steps in this guide, which you must customize for your particular environment, describe how to recover the entire Active Directory forest to a point in time before the critical malfunction. They also ensure that none of the restored domain controllers replicates from a domain controller with potentially dangerous data. The procedures apply to Active Directory Domain Services (AD DS) in Windows Server 2012, Windows Server 2008 R2, Windows Server 2008, and the Active Directory® directory service in Windows Server 2003.
The white paper is available here : Windows Server 2012: Planning for Active Directory Forest Recovery
This guide contains best-practice recommendations for recovering an Active Directory forest, if forest-wide failure has rendered all domain controllers in the forest incapable of functioning normally. The procedure steps in this guide, which you must customize for your particular environment, describe how to recover the entire Active Directory forest to a point in time before the critical malfunction. They also ensure that none of the restored domain controllers replicates from a domain controller with potentially dangerous data. The procedures apply to Active Directory Domain Services (AD DS) in Windows Server 2012, Windows Server 2008 R2, Windows Server 2008, and the Active Directory® directory service in Windows Server 2003.
The white paper is available here : Windows Server 2012: Planning for Active Directory Forest Recovery
mardi 30 avril 2013
[Active Directory] Active Directory Considerations in Azure Virtual Machines and Virtual Networks Blog Series
Thomas W Shinder has published a 5 parts blog series on Active Directory Considerations in Azure Virtual Machines and Virtual Networks.
Here is the blog's series :
Here is the blog's series :
- Active Directory Considerations in Azure Virtual Machines and Virtual Networks Part 1 – Hybrid IT
- Active Directory Considerations in Azure Virtual Machines and Virtual Networks Part 2 – Azure Virtual Machines and Virtual Networks Basics
- Active Directory Considerations in Azure Virtual Machines and Virtual Networks Part 3 - Virtual DCs and AD File Placement
- Active Directory Considerations in Azure Virtual Machines and Virtual Networks Part 4 – RODCs and Site Considerations
- Active Directory Considerations in Azure Virtual Machines and Virtual Networks Part 5 – Domains and GCs
- Active Directory Considerations in Azure Virtual Machines and Virtual Networks – Part 6 – Name Resolution and Geo-distribution
lundi 29 avril 2013
[Active Directory] Best Practices for Securing Active Directory White Paper
Microsoft has published a new white paper named Best Practices for Securing Active Directory.
This document contains recommendations to assist organizations in enhancing the security of their Active Directory installations. By implementing these recommendations, organizations will be able to identify and prioritize security activities, protect key segments of their organization’s computing infrastructure, and create controls that significantly decrease the likelihood of successful attacks against critical components of the IT environment. This document discusses the most common attacks against Active Directory and countermeasures to reduce the attack surface, and recommendations for recovery in the event of complete compromise.
The white paper is available here : Best Practices for Securing Active Directory
This document contains recommendations to assist organizations in enhancing the security of their Active Directory installations. By implementing these recommendations, organizations will be able to identify and prioritize security activities, protect key segments of their organization’s computing infrastructure, and create controls that significantly decrease the likelihood of successful attacks against critical components of the IT environment. This document discusses the most common attacks against Active Directory and countermeasures to reduce the attack surface, and recommendations for recovery in the event of complete compromise.
The white paper is available here : Best Practices for Securing Active Directory
lundi 22 avril 2013
Who Wants to Be an AD Expert ? Blogroll and other Stuff
Hi,
Before starting this blog series I would share some links to blog related to Active Directory and other links like Technet, MSDN, Wiki, Forum, ...
This list isn't exhaustive and will evolve over time.
Microsoft Blog :
Ask The Directory Services Team : http://blogs.technet.com/b/askds/
Active Directory Documentation Team : http://blogs.technet.com/b/activedirectoryua/
AD Troubleshooting : http://blogs.technet.com/b/instan/
AD RMS Team Blog : http://blogs.technet.com/b/rms/
Windows PKI blog : http://blogs.technet.com/b/pki/
Group Policy Blog : http://blogs.technet.com/b/grouppolicy/
Windows Azure Active Directory Graph Team : http://blogs.msdn.com/b/aadgraphteam/
Group Policy Central : http://www.grouppolicy.biz/
Ask Premier Field Engineering (PFE) Platforms : http://blogs.technet.com/b/askpfeplat/
Goatee PFE : http://blogs.technet.com/b/ashleymcglone/
Canberra Premier Field Engineering Team Blog : http://blogs.msdn.com/b/canberrapfe/
Premier Field Engineering : http://blogs.technet.com/b/mspfe/
Bruce Adamczak : http://blogs.technet.com/b/bruce_adamczak
Rob Bolbotowski : http://blogs.technet.com/b/robertbo/
Glenn LeCheminant : http://blogs.technet.com/b/glennl/
Jane Lewis : http://blogs.technet.com/janelewis
Mark Empson : http://blogs.technet.com/b/mempson/
Mark Morowczynski : http://blogs.technet.com/b/markmoro/
Matheesha Weerasinghe : http://blogs.technet.com/b/maweeras/
Ben Pearce : http://blogs.technet.com/b/benp/
Other Blogs :
Brian Desmond's Blog : http://briandesmond.com/blog/
The Swede's blog : http://jimmytheswede.blogspot.fr/
Joe Richard’s blog : http://blog.joeware.net/
Sander Berkouwer's Blog : http://blogs.dirteam.com/blogs/sanderberkouwer/default.aspx
Ulf B. Simon-Weidner's Blog : http://msmvps.com/blogs/ulfbsimonweidner/default.aspx
Mike Kline's Blog : http://adisfun.blogspot.fr/
Paul Bergson's Blog : http://blogs.dirteam.com/blogs/paulbergson/default.aspx
DSA Blog : http://dsablog.com/
Jorge's Quest For Knowledge : http://jorgequestforknowledge.wordpress.com/
Christoffer Andersson' Blog : http://blogs.chrisse.se/
ADdict : http://setspn.blogspot.co.uk/
Florian’s Blog : http://www.frickelsoft.net/blog/
Tomek's DS World : http://blogs.dirteam.com/blogs/tomek/default.aspx
Sean Metcalf's Blog : http://blogs.metcorpconsulting.com/tech/
Mark Parris's Blog : http://markparris.co.uk/
Santhosh Sivarajan's Blog : http://portal.sivarajan.com/
Open a Socket! : http://www.open-a-socket.com/
Activedir.org : http://www.activedir.org/List.aspx
Shariq Sheikh's Blog : http://www.shariqsheikh.com/blog/
John Policelli's Blog : http://policelli.com/blog/
Clint Boessen's Blog : http://clintboessen.blogspot.fr/
Meinolf Weber's Blog : http://msmvps.com/blogs/mweber/
Sandesh Dubey's Blog : http://sandeshdubey.wordpress.com/
Awinish's Technical Blog : http://awinish.wordpress.com/
Abhijit's Blog : http://abhijitw.wordpress.com/
Wiki :
Active Directory Wiki : http://social.technet.microsoft.com/wiki/tags/Active+Directory/default.aspx
Technet and MSDN :
Active Directory Services : http://technet.microsoft.com/en-us/library/dd578336%28v=ws.10%29.aspx
Active Directory Domain Services : http://msdn.microsoft.com/en-us/library/aa362244%28v=vs.85%29.aspx
Technet Forum :
Directory Services : http://social.technet.microsoft.com/Forums/en-us/winserverDS/threads
Group Policy : http://social.technet.microsoft.com/Forums/en-us/winserverGP/threads
Migration : http://social.technet.microsoft.com/Forums/en-us/winserverMigration/threads
Channel 9 :
Active Directory Channel 9 : http://channel9.msdn.com/search?term=Active+Directory
Before starting this blog series I would share some links to blog related to Active Directory and other links like Technet, MSDN, Wiki, Forum, ...
This list isn't exhaustive and will evolve over time.
Microsoft Blog :
Ask The Directory Services Team : http://blogs.technet.com/b/askds/
Active Directory Documentation Team : http://blogs.technet.com/b/activedirectoryua/
AD Troubleshooting : http://blogs.technet.com/b/instan/
AD RMS Team Blog : http://blogs.technet.com/b/rms/
Windows PKI blog : http://blogs.technet.com/b/pki/
Group Policy Blog : http://blogs.technet.com/b/grouppolicy/
Windows Azure Active Directory Graph Team : http://blogs.msdn.com/b/aadgraphteam/
Group Policy Central : http://www.grouppolicy.biz/
Ask Premier Field Engineering (PFE) Platforms : http://blogs.technet.com/b/askpfeplat/
Goatee PFE : http://blogs.technet.com/b/ashleymcglone/
Canberra Premier Field Engineering Team Blog : http://blogs.msdn.com/b/canberrapfe/
Premier Field Engineering : http://blogs.technet.com/b/mspfe/
Bruce Adamczak : http://blogs.technet.com/b/bruce_adamczak
Rob Bolbotowski : http://blogs.technet.com/b/robertbo/
Glenn LeCheminant : http://blogs.technet.com/b/glennl/
Jane Lewis : http://blogs.technet.com/janelewis
Mark Empson : http://blogs.technet.com/b/mempson/
Mark Morowczynski : http://blogs.technet.com/b/markmoro/
Matheesha Weerasinghe : http://blogs.technet.com/b/maweeras/
Ben Pearce : http://blogs.technet.com/b/benp/
Other Blogs :
Brian Desmond's Blog : http://briandesmond.com/blog/
The Swede's blog : http://jimmytheswede.blogspot.fr/
Joe Richard’s blog : http://blog.joeware.net/
Sander Berkouwer's Blog : http://blogs.dirteam.com/blogs/sanderberkouwer/default.aspx
Ulf B. Simon-Weidner's Blog : http://msmvps.com/blogs/ulfbsimonweidner/default.aspx
Mike Kline's Blog : http://adisfun.blogspot.fr/
Paul Bergson's Blog : http://blogs.dirteam.com/blogs/paulbergson/default.aspx
DSA Blog : http://dsablog.com/
Jorge's Quest For Knowledge : http://jorgequestforknowledge.wordpress.com/
Christoffer Andersson' Blog : http://blogs.chrisse.se/
ADdict : http://setspn.blogspot.co.uk/
Florian’s Blog : http://www.frickelsoft.net/blog/
Tomek's DS World : http://blogs.dirteam.com/blogs/tomek/default.aspx
Sean Metcalf's Blog : http://blogs.metcorpconsulting.com/tech/
Mark Parris's Blog : http://markparris.co.uk/
Santhosh Sivarajan's Blog : http://portal.sivarajan.com/
Open a Socket! : http://www.open-a-socket.com/
Activedir.org : http://www.activedir.org/List.aspx
Shariq Sheikh's Blog : http://www.shariqsheikh.com/blog/
John Policelli's Blog : http://policelli.com/blog/
Clint Boessen's Blog : http://clintboessen.blogspot.fr/
Meinolf Weber's Blog : http://msmvps.com/blogs/mweber/
Sandesh Dubey's Blog : http://sandeshdubey.wordpress.com/
Awinish's Technical Blog : http://awinish.wordpress.com/
Abhijit's Blog : http://abhijitw.wordpress.com/
Wiki :
Active Directory Wiki : http://social.technet.microsoft.com/wiki/tags/Active+Directory/default.aspx
Technet and MSDN :
Active Directory Services : http://technet.microsoft.com/en-us/library/dd578336%28v=ws.10%29.aspx
Active Directory Domain Services : http://msdn.microsoft.com/en-us/library/aa362244%28v=vs.85%29.aspx
Technet Forum :
Directory Services : http://social.technet.microsoft.com/Forums/en-us/winserverDS/threads
Group Policy : http://social.technet.microsoft.com/Forums/en-us/winserverGP/threads
Migration : http://social.technet.microsoft.com/Forums/en-us/winserverMigration/threads
Channel 9 :
Active Directory Channel 9 : http://channel9.msdn.com/search?term=Active+Directory
Inscription à :
Articles (Atom)