We have to :
- Enable support for claims and compound authentication by using Group Policy
- Enable claim for devices by using Group Policy
- Apply the central access policy across file servers by using Group Policy
- Assign a central access policy to the file server
To enable support for claims and compound authentication we'll edit the Default Domain Controller Policy.
We have to edit only one setting.
Now, we have to enable claim for devices by editing the Default Domain Policy.
Now we have to apply the Central Access Policy we have created earlier on the File Server by creating a new GPO.
That's all for the Group Policy part.
Now we have to assign the Central Access Policy to the File Server.
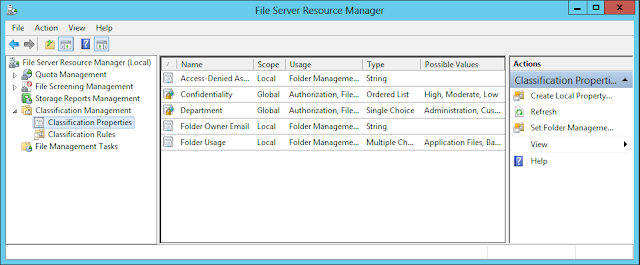
First we have to refresh the Global Ressource Properties. This can be done with Powershell or through FSRM.
If you go on the Classification Properties, you can see that we have our two Ressource Properties, Department and Confidentiality.
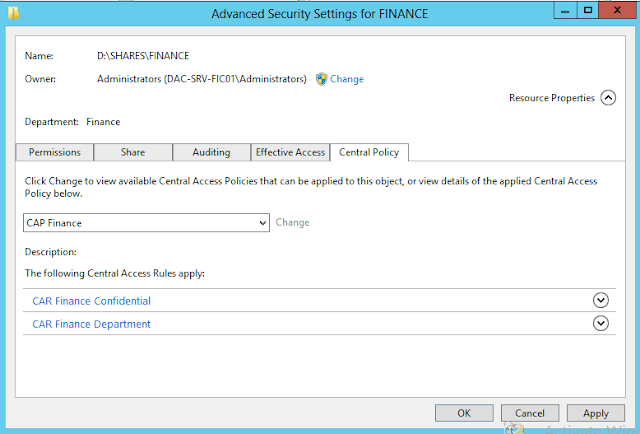
Now I go on the Finance folder to apply the Central Access Policy.
First I configure manually the Department classification on the Finance folder.
Then I apply the Central Access Policy.
I do the same for the CONFIDENTIAL sub-folder, add the confidentiality classification to High.
The Central Access Policy and the Department classification is inherited from the parent folder.
Now we can verify that DAC is well implemented.
First, I will check that claim is enable for users. It can be done with the command : whoami /claims
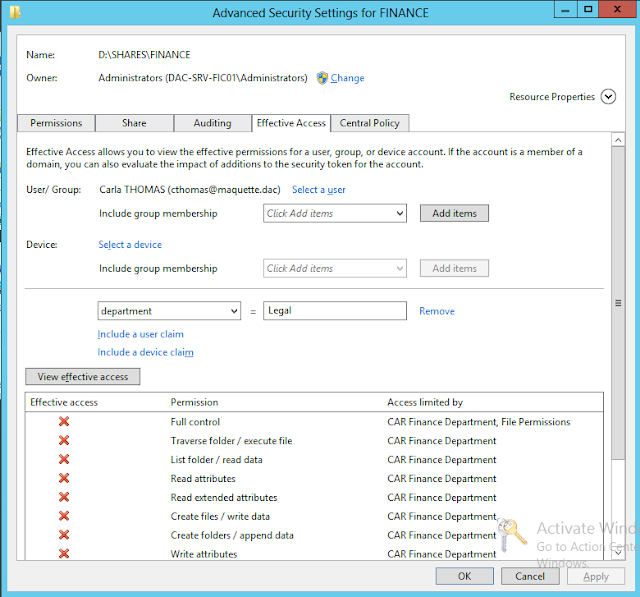
We can now verify the effective access on the folder.
First at the Finance folder level with Carla Thomas.
We can see that the user has RW access.
Now I change the user claim and we can see that the user doesn't have access and this access is limited by CAR Finance Department.
Now we go on the Confidential sub-folder.
The Confidential CAR require that the user and the device are from the Finance department and that the user is a member of the Confidential group.
If we modify the device claim we loose access.
That's all for the Central Access Policy part which is only one of the features of Dynamic Access Control.
If you want more information on this part check this : http://technet.microsoft.com/en-us/library/hh831425
We'll see next Access-Denied Assistance feature.















Aucun commentaire:
Enregistrer un commentaire